Empire

Empire is a pure
PowerShellpost-exploitationagent built oncryptologically-securecommunications and a flexible architecture.
Empire implements the ability to run PowerShell agents without needing powershell.exe, rapidly deployable post-exploitation modules ranging from
key loggerstoMimikatz, andadaptablecommunications toevadenetwork detection, all wrapped up in a usability-focused framework.
Here is a short note from GIAC about Empire
traffic.
Identifying Empire C2 traffic is an inherently difficult task. Empire C2 traffic is designed to be both
stealthyandsecure. Empire accomplishes this byencryptingits communications,mirroringHTTP activity, and by making in frequent and jittered(slightly randomized)connections(Schroeder, & Warner, 2015).

This thing about encrypting our traffic on the C2, I would like to think that most pentesters know this, it is clear that in the post-exploitation phase, you may come across important data, be it employee addresses, payments, etc. It would not be a good idea to exfiltrate such data over an unencrypted connection. this could lead to many problems and could even harm third persons. You don’t know if you are the only one in the network.
StarKiller
Starkiller is a
FrontendforPowershell Empire. It is anElectronapplication written inVueJS.
Multi-userGUIapplication for interfacing with theEmpireC2serverfrom any computer.
The good thing about this is that several members of a red team can connect to your server, which speeds up the post-exploitation phase.
> Gif Source: BC-Security
For this test, we will use starkiller.
If you are on a red team compromise, it would be recommended to install empire, on a vps accessed via proxy, vpn, etc.
Installation
The installation is very simple, we just have to use a repository.
sudo apt install powershell-empire starkiller
Setup-Server
With empire & starkiller installed, we now need to start Empire server.
sudo su
powershell-empire server

Once this is done, we can start starkiller
sudo su
starkiller &
disown
> The disown command is a part of the Unix ksh, bash, and zsh shells and is used to remove jobs from the current shell.

Well, at this point we need to open a
.yamlconfigfile, to change the default credentials that Empire comes with.
cat /usr/share/powershell-empire/empire/client/config.yaml

Listeners
Well, for this test we are going to see how to launch a
sessionfrom thevictimmachine toempire.
First we need to create a
listener.

We are going to focus on creating an
httpsconnection to be more secure.

If we read the official documentation of
powershellempireabout the listeners, we can see that they already explain and provide us with a script to create a .pem.
“For HTTPS listeners, you must first set the CertPath to be a local .pem file. The provided
./setup/cert.shscript will generate a self-signed cert and place it in./data/empire.pem.”

Instead of downloading the script, we directly copy the command, generate our .pem, and put the path “/path/to/” in our listener.
openssl req -new -x509 -keyout empire-priv.key -out empire-chain.pem -days 365 -nodes -subj "/C=US" >/dev/null 2>&1


Stagers
Well, now that we have our listener ready, let’s proceed to generate a stager.
As before, right window, click on stagers and in the upper right corner, click on create.
Here we see many types of stagers, but for this test, we are going to use something simple, a
.batscript

In this test we are simply using a bat script.
Once created, we now download it.

I have assumed that you have already found a way to launch the script as stealthily as possible to give you a session.
Once that is done, we have an
agentto interact with.
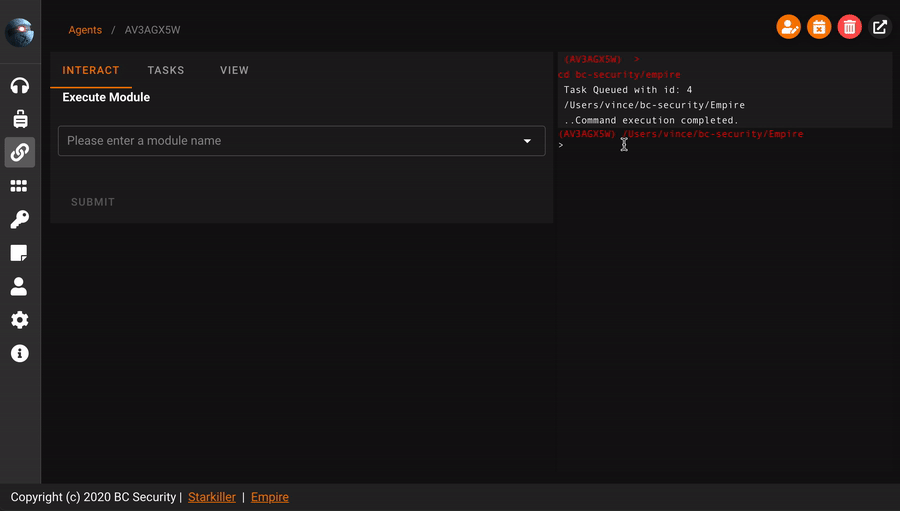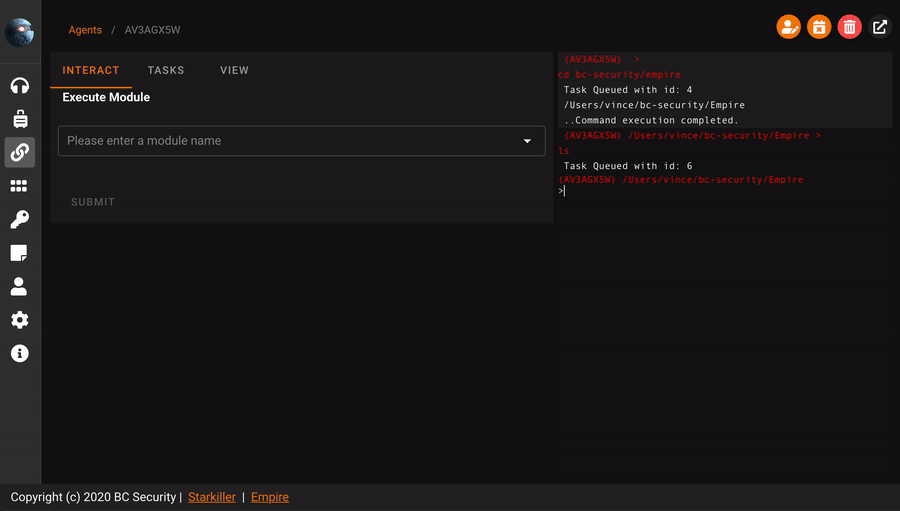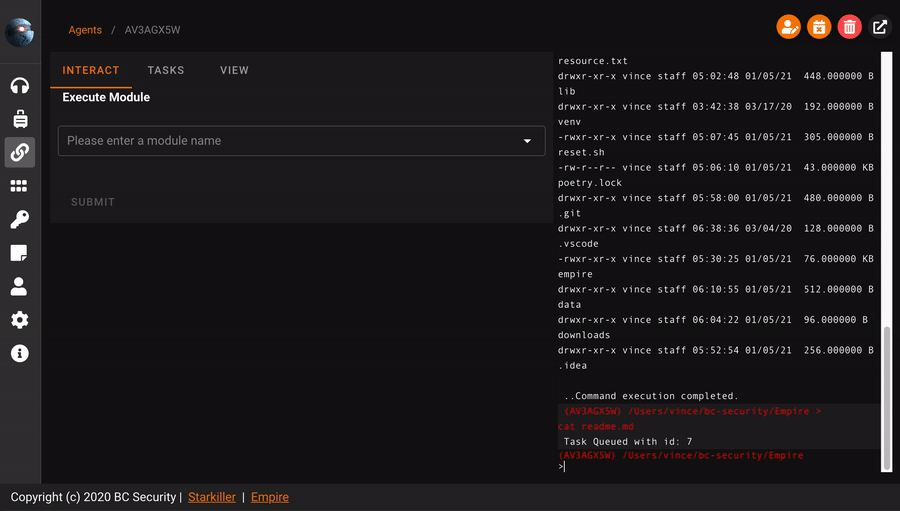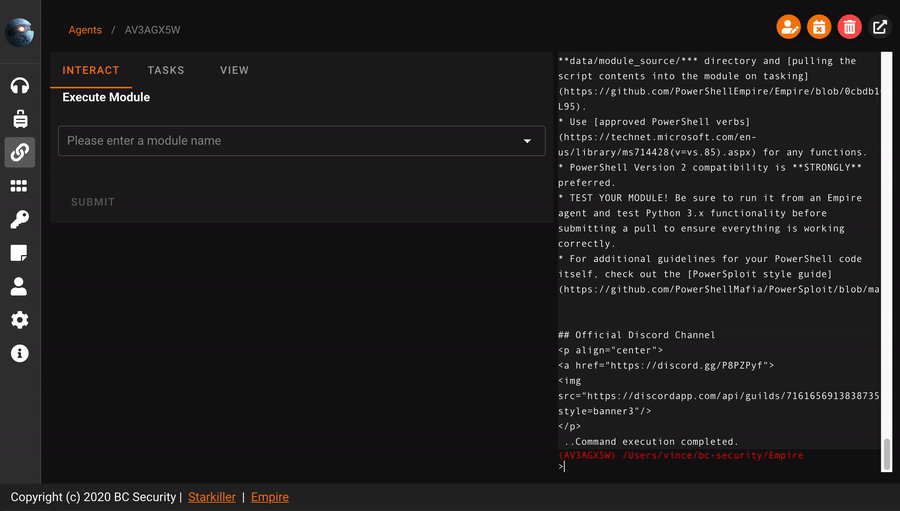
Agent
To interact with an agent, it’s easy, just go to the left, click on agents

And simply click on the agent
name.

From here, you can start enumerating your victim, for example let’s launch the following command
systeminfo
Once the command is launched, go to
taskand you will see the output of the command.

note, for example you can take that information, simply paste it in some .txt on your machine and use
windows exploit suggester, it doesn’t make any noise since you are launching it on your machine and it takes care of querying a local database.
Even if you don’t like to list files by command line, just go to the
"File Browser"and you will see all files in the system graphically.

Modules
Undoubtedly, Empire has some very interesting modules, such as
objectacl,mimikatz,lsadump,keylogger,gpp, etc…
I think that here you have realized the importance of C2, not only for its encrypted channels and easy installation, but for its way of representing the information, the ease of interacting with the victim, you just have to find the module and launch it and empire will do the “dirty” work for you.
For this test, obviously we are not going to use all the modules since there are many, to show it we are simply going to use the module
Watson
Watson is a
.NETtool designed to enumerate missing KBs and suggest exploits for Privilege Escalation vulnerabilities.
Run it is a very simple task.
