ARP-SPOOFING

In this article we will see how to obtain
credentialsincleartext, through anarp spoofingattack
All tests in this article will be performed at the INE free lab.
ARP
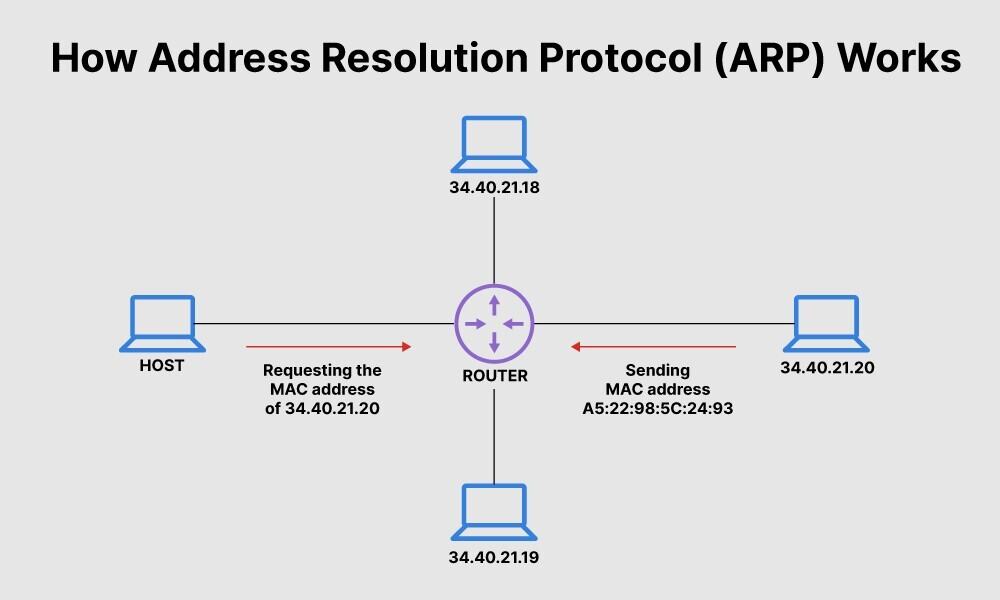
Image Src: Fortinet
The address resolution protocol
(ARP)is a data link layer communications protocol responsible for finding the(MAC)hardware address that corresponds to a givenIPaddress. This is done by sending an(ARP request)packet to the network broadcast address(broadcast, MAC = FF FF FF FF FF FF FF FF FF FF FF FF FF)containing the IP address being queried, and waiting for that(or another)machine to reply(ARP reply)with the Ethernet address that corresponds to it.
ARP-SPOOF
(MitM)Usually the purpose is toassociatethe attacker’sMACaddress with theIPaddress of another node(the attacked node), such as the default gateway. Any traffic directed to that node’s IP address will be mistakenlysentto the attacker, rather than to its actual destination.
To execute this attack i am going to use my
ArpSpoofing-Autotool writen inbash, which automates thesniffingprocess with theArpSpoofandtsharktools, to give you a.pcapfile to analyze withwireshark.
-
Identify the telnet server and the client machine
-
Intercept traffic between the two
-
Analyze the traffic and steal valid credentials

- 10.100.13.37 server, 10.100.13.36 client
Arp-Spoofing Tool
wget https://raw.githubusercontent.com/HI0U/ArpSpoofing-Auto/main/Auto-arp.sh
chmod +x Auto-arp.sh
./Auto-arp.sh

Once we get that capture, you can analyze it in
wiresharkto get thecredentialsand connect to the server viatelnet.
